Well, over the holidays, my website was hacked once again. This is the third time in as many months this has happened.
Apparently, I wasn’t the only one affected. My hosting company, who this time were kind enough to warn me about the issue, maintains that the hacker somehow obtained my FTP password. Myself, I’m beginning to suspect that there’s a vulnerability in Apache Server which has yet to be addressed. The nature of the hack suggests that a kind of worm, or other unintelligent automated process, was to blame for the attack. It acted much like the “F*ck PoizonBox” worm which struck millions of websites a few years ago. It only targeted a certain kind of files, rewriting them in a manner that suggests very clumsy automation.
Nevertheless, I changed the password and replaced the affected files. For now, the ScamWatch blog will have to act as the front page for my website, which is maybe just as well, since the old one was, frankly, embarrassing.
What did the hack do?
It did two things: rewrite certain HTML files so as to inject a hidden IFRAME into the document, one which loaded a parameterized URL to a known hacker site.
The second thing it did was to tamper with the default actions of the site, so that any broken URL’s would cause a redirection to aforementioned site. This is more nefarious, since for example trying to browse any unindexed folder via a raw URL would cause a 403 error, which would send you to the malicious site.
Once there, you would be subjected to false alerts about a possible infection, and offered to download a solution… which, naturally, woúld have flooded your system with spyware. Sigh!
Why did they do it?
At first, I suspected a case of retalliation. Fighting the crooks who spread spyware and malware makes me and my site a natural target for certain kinds of payback attack. It was naive of me not to expect it. I’m just surprised it didn’t happen sooner.
However, the nature of the attack, and the fact that I’m not alone to have suffered, suggest that it wasn’t personal. It seems that the script kiddies (read: stupid hacker snotnoses) are having a harvesting contest to count how many sites they can compromise. It’s one of the many ways they have of comparing their tiny penises.
Have any visitors been affected? Is there a risk coming here?
Fortunately, no. The hacks were so blatantly stupid and badly written that they couldn’t have worked in any browser. Cleaning them up is a nuisance, but they aren’t dangerous to visitors. Not ones who know what they’re doing.
The broken URL hack, however, would have worked. I tested it myself on a sandboxed computer to see what would happen in certain scenarios. It has now been fixed.
Has UnZixWin, or any other software, been compromised?
Nope. None of the downloads have been tampered with. They are still safe to download and install.
What are you going to do about it?
On the bright side, it has rekindled my faltering interest in online security once more. After a post-mortem analysis of their tricks, I’m considering a multi-pronged defence mechanism constituting of the following:
* A daily, scheduled, automated system to check the health of my sites to detect and repair any tampered files
* A script, included everywhere, to automatically detect and remove hostile IFRAMEs before they have any chance of triggering.
* A new article, detailing the hacks in technical detail
And, while I’m in the process of doing all that,
* A major overhaul of the whole site. It has been long overdue.
Watch this space.
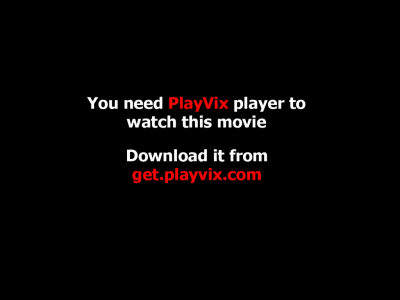 Beware! It’s yet another form of the old DivoCodec scam, this time with a new twist.
Beware! It’s yet another form of the old DivoCodec scam, this time with a new twist.